PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1644432

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1644432
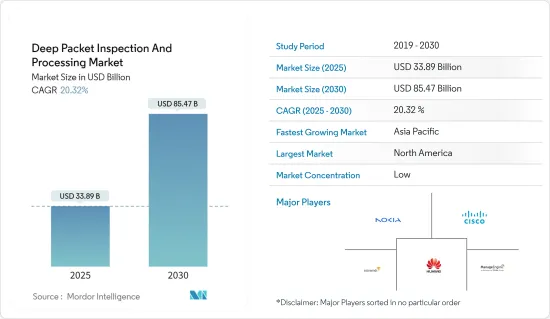
Deep Packet Inspection And Processing - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030)
The Deep Packet Inspection And Processing Market size is estimated at USD 33.89 billion in 2025, and is expected to reach USD 85.47 billion by 2030, at a CAGR of 20.32% during the forecast period (2025-2030).
DPI combines signature matching technology with a data analysis algorithm to determine a communication stream impact. Hardware-based middleboxes are prevalent in computer networks, which usually incur high deployment and management expenses.
Key Highlights
- A recent trend addresses those problems where researchers propose two practical approaches to implement a cloud-based DPI middlebox. The outsourced DPI middlebox performs payload inspection over encrypted traffic while preserving the privacy of both communication data and inspection rules.
- The proliferation of technologies, such as cloud deployment, remote working, BYOD, SaaS applications, etc., are increasing the paths available to cyberattacks. Applications have become inviting targets for cybercriminals, but securing, protecting, and controlling the networks that connect them is a huge challenge for network security providers.
- In contrast, DPI in the European Union is used very differently. It is used as part of mechanisms to clamp down on drug trafficking and child pornography. When the EU established its intent, they were quick to enforce laws that controlled the use of data. The consideration falls under the General Data Protection Regulation (GDPR), a comprehensive set of laws protecting EU citizens and their sensitive data.
- With the growing global IP traffic augmented by mobile devices, the emergence of the Internet of Things (IoT) and cloud computing require close attention and powerful tools to ensure secure operations on an enterprise network.
- Many cloud services are accessible to the entire internet, which means improved system accessibility is an important driver for cloud migrations. However, cloud servers and applications are regularly attacked using various methods from anywhere globally. Deep packet inspection and processing are essential to keep the bad traffic out while letting the good traffic through without too much interruption. It is also important to look beyond this perimeter-based defense layer. There are several approaches to successfully deploying a security control based on Deep Packet Inspection within a public cloud environment, such as using the vendor solutions already built for this exact purpose, and another product range is based on agents running on customer endpoints.
- Moreover, attackers started exploiting the burst of information and heightened public alertness for COVID-19-related news. Phishing, spam campaigns, and malicious websites/domains significantly increased. To relieve the load on VPNs and mitigate the chances of successful command and control (C2) channels for malware to be established, F-Secure recommends using deep packet inspection on VPN concentrators and other network perimeter devices. Certain bandwidth-heavy online services, such as streaming and various gaming services, can be blocked with such a stand. It is also recommended to allow communication on only known and approved ports, such as HTTPS. The pandemic is significantly increasing the adoption rate.
Deep Packet Inspection and Processing Market Trends
Software Solution to Witness Significant Growth With Increasing Enterprise Internet Traffic
- In recent years, DPI (Deep Packet Inspection) software has evolved into a powerful tool to meet new network challenges, playing a central role in today's internet and network infrastructure. As most internet traffic is now encrypted, a reliable DPI software engine needs a tool kit of advanced techniques to classify traffic.
- DPI identifies and classifies traffic based on the signature database that includes information extracted from the data part of a packet, allowing finer control than classification based only on header information. Applications such as peer-to-peer (P2P) traffic provide increasing problems for broadband service providers.
- Typically, P2P traffic is used by applications providing file sharing. Due to its frequently large size of media files being transferred, P2P drives the increasing traffic loads, which requires additional network capacity. DPI allows operators to oversell their available bandwidth while ensuring equitable bandwidth distribution to all users by preventing network congestion.
- The network must be able to parse through content, assemble enough of an application message, and identify traffic usage and patterns based on the information. DPI functions fall into four categories: Protocol analysis/application recognition, Anti-malware/anti-virus, Intrusion Detection and Prevention (IDS/IPS), and URL filtering.
- According to the Enea AB survey, 70 percent of respondents (high-tech product managers) require the classification of connected devices in the enterprise and IoT/industrial networks. And also, the increased use of encryption and the adoption of the stringent TLS 1.3 security protocol (mandatory in 5G) threatens essential traffic visibility for many vendors. This requires Deep packet inspection and processing catering to future market growth.
- Further, most vendors report that they have or are developing cloud solutions, with half planning to offer a Secure Access Service Edge (SASE) solution that integrates security and networking in a cloud-based service. This requires the use of DPI software, which adheres to market growth.
North America Accounts for the Significant Market Share
- The deep packet inspection and processing market has grown in Asia Pacific significantly in recent years. DPI technology enables the inspection and analysis of data packets passing through a network, providing insights into the content and context of network traffic. Enhancing network security, optimizing network performance, and enabling advanced services such as Quality Services and traffic management is crucial.
- The region is expected to grow substantially in the DPI market in the coming years. The demand is characterized by the rising adoption of advanced technologies, including 5G, IoT, and cloud computing, which generate massive data traffic. DPI technology enables network administrators and service providers to gain granular visibility and control over this data, ensuring efficient network management and enhanced user experiences.
- Network traffic analysis and management With the exponential growth in data traffic, network operators require advanced tools to analyze and manage network flows effectively. DPI technology provides granular insights into network behavior, enabling operators to optimize bandwidth allocation and enhance network performance.
- Different industries, like healthcare and finance, are subject to strict data privacy and security regulations. DPI technology ensures compliance by inspecting network traffic for policy violations and unauthorized access attempts.
- The proliferation of IoT devices and the adoption of industrial automation solutions in the region also drive the demand for DPI technology. DPI enables real-time analysis of IoT device traffic, delivering secure and reliable communication between devices and data centers.
- The emergence of the 5G network presents significant opportunities for DPI technology. With its high bandwidth, low latency, and massive connection density, 5G networks generate vast amounts of data traffic that require efficient management and analysis.
Deep Packet Inspection and Processing Industry Overview
The deep packet inspection and processing market is fragmented as the players are increasingly innovating new hardware and software solutions, and also new entrants are adding to this market that caters to the significant competition. Several innovations have been witnessed in the deep packet inspection and processing market, including developing Next-Generation Firewalls (NGFWs) that can investigate the network packets up to 7 application layers of the OSI model. Such instances provide intense rivalry among the players to provide unique solutions. Nokia (Alcatel Lucent), SolarWinds Worldwide, LLC, cisco systems, and Huawei Technologies are key players. Recent developments in the market are -
- February 2023 - Cisco announced plans to purchase Lightspin, an Israeli cloud security business. Cisco and Lightspin will achieve their mutual goal of assisting customers in modernizing their cloud infrastructures by providing end-to-end security and observability from construction to runtime.
- January 2023 - ipoque GmbH, a Rohde & Schwarz company, and APCON, Inc., a US-based network visibility and security services provider for data centers, announced their new partnership. The agreement specifies the advanced deep packet inspection (DPI) software library from Epoque, R&S(R)PACE 2, as a licensable add-on software tool for the IntellaView HyperEngine hardware platform (HyperEngine) from APCON.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Buyers/Consumers
- 4.3.2 Bargaining Power of Suppliers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Regulatory Implications
- 4.5 Assessment of COVID-19 Impact on the Market
- 4.6 Market Drivers
- 4.6.1 Increasing Adoption of Regulatory and Data Protection Laws
- 4.6.2 High Adoption of Cloud Based Security Technologies
- 4.7 Market Restraints
- 4.7.1 DPI Adds to the Complexity and Unwieldy Nature of Existing Firewalls and Other Security-Related Software
5 MARKET SEGMENTATION
- 5.1 Solution
- 5.1.1 Hardware
- 5.1.2 Software
- 5.2 Deployment
- 5.2.1 On-Premise
- 5.2.2 Cloud
- 5.3 End-User
- 5.3.1 Telecom and IT
- 5.3.2 BFSI
- 5.3.3 Healthcare
- 5.3.4 Retail
- 5.3.5 Other End-Users
- 5.4 Geography
- 5.4.1 North America
- 5.4.1.1 United States
- 5.4.1.2 Canada
- 5.4.2 Europe
- 5.4.2.1 Germany
- 5.4.2.2 United Kingdom
- 5.4.2.3 France
- 5.4.2.4 Rest of Europe
- 5.4.3 Asia-Pacific
- 5.4.3.1 China
- 5.4.3.2 Japan
- 5.4.3.3 Australia
- 5.4.3.4 Rest of Asia-Pacific
- 5.4.4 Latin America
- 5.4.5 Middle East and Africa
- 5.4.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 Nokia Corporation (Alcatel Lucent)
- 6.1.2 Allot Ltd.
- 6.1.3 Bivio Networks, Inc.
- 6.1.4 Huawei Technologies Co., Ltd.
- 6.1.5 Enea AB (Qosmos SA)
- 6.1.6 WiseSpot Company Limited
- 6.1.7 SolarWinds Worldwide, LLC.
- 6.1.8 NetFort Technologies Limited (Rapid7
- 6.1.9 Netify
- 6.1.10 AppNeta, Inc.
- 6.1.11 ManageEngine (Zoho Corporation)
- 6.1.12 Cisco Systems, Inc.
- 6.1.13 ipoque GmbH
7 INVESTMENT ANALYSIS
8 MARKET OPPORTUNITIES AND FUTURE TRENDS




