PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1630340

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1630340
Data Exfiltration - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030)
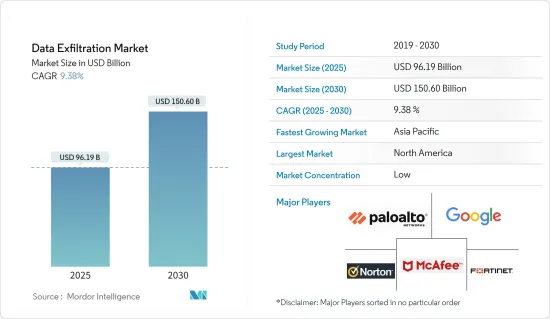
The Data Exfiltration Market size is estimated at USD 96.19 billion in 2025, and is expected to reach USD 150.60 billion by 2030, at a CAGR of 9.38% during the forecast period (2025-2030).
Data exfiltration is a security breach that occurs when sensitive information from an organization is transferred or copied without authorization from a server or a computer to a location controlled by a threat actor. It is primarily a targeted attack in which the hacker's primary goal is to copy and extract specific information from the data. Hackers directly access the targeted system via remote programs or by installing a portable media device. Personal health information, intellectual property or trade secrets of a firm, personally identifiable information, and financial information, such as credit card or bank details, are all large data breaches.
Key Highlights
- The increasing volumes of enterprise data often contain valuable assets such as customer information, intellectual property, trade secrets, financial records, and other sensitive data. This makes organizations attractive targets for data exfiltration attacks. Protecting these valuable assets drives the demand for advanced prevention solutions.
- Strict regulatory requirements for data protection play a crucial role in driving the need for data exfiltration prevention. Various data protection regulations, such as the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and other regional or industry-specific regulations, mandate organizations to implement measures to protect sensitive data from unauthorized access, including data exfiltration. Compliance with these regulations is crucial to avoid legal penalties, reputational damage, and loss of customer trust.
- Increasing data loss incidents in the on-premises environment can drive the need for data exfiltration prevention. On-premises environments may have complex and interconnected IT systems, which can introduce vulnerabilities. Malicious actors can exploit these vulnerabilities to gain unauthorized access and exfiltrate sensitive data. The increasing data loss incidents in on-premises environments highlight the need for robust data exfiltration prevention solutions to protect against such threats.
- Compatibility issues between on-premises applications and the cloud environment can pose challenges and restrain the data exfiltration prevention market. Ensuring comprehensive data visibility and monitoring in a hybrid environment where on-premises applications interact with cloud services can be challenging. Data exfiltration prevention solutions often rely on monitoring network traffic, user behavior, and data access patterns to detect and prevent unauthorized data transfers. However, compatibility issues may hinder seamless monitoring across on-premises and cloud environments, limiting the effectiveness of data exfiltration prevention measures.
- The COVID-19 pandemic significantly impacted various aspects of the cybersecurity landscape, including the data exfiltration market. With the increased adoption of remote work during the pandemic, organizations rapidly adjusted their IT infrastructure and security measures. This sudden shift introduced new vulnerabilities and challenges, as remote work environments were expected to have different security controls than traditional on-premises setups. Attackers exploited these vulnerabilities to target remote workers and gain unauthorized access to sensitive data, increasing the risk of data exfiltration.
Data Exfiltration Market Trends
Healthcare and Life Sciences End User Segment is Expected to Hold Significant Market Share
- Data exfiltration is a significant concern in the healthcare and life sciences industry due to the sensitive nature of the data involved, such as patient medical records, clinical trial data, intellectual property, and proprietary research. Unauthorized access to this data can lead to severe consequences, including patient privacy breaches, reputational damage, regulatory non-compliance, and compromised research and development efforts.
- Protecting patient data is a top priority in the healthcare industry. Personal health information (PHI) and electronic health records (EHRs) contain highly sensitive information and are attractive targets for cybercriminals. Data breaches in healthcare can result in identity theft, insurance fraud, and other serious consequences for patients.
- Increasing ransomware attacks can directly impact the prevalence and scale of data exfiltration incidents. According to IC3 and FBI, In 2022, the U.S. Internet Crime Complaint Center (IC3) received 210 complaints indicating ransomware attacks on healthcare organizations globally.
- The healthcare industry is subject to various regulations and data protection standards, including the Health Insurance Portability and Accountability Act (HIPAA) in the United States and the General Data Protection Regulation (GDPR) in the European Union. These regulations mandate strict controls and protocols for safeguarding patient data, including measures to prevent data exfiltration.
- The healthcare and life sciences industry faces a diverse range of cyber threats. These include ransomware attacks, phishing attempts, social engineering, malware infections, and insider threats. Threat actors may target healthcare organizations to steal valuable data, disrupt operations, or extort ransom payments.
North America is Expected to Hold Significant Market Share
- Data exfiltration is a significant concern in North America. North America houses many organizations across various industries, making it an attractive target for cybercriminals seeking to steal sensitive data for financial gain, espionage, or other malicious purposes.
- North America has seen the emergence of numerous cybercriminal groups, both domestic and international, engaged in data exfiltration activities. These groups may have different motivations, such as financial gain, political agendas, or state-sponsored espionage. They use sophisticated techniques, tools, and tactics to defy security defenses and steal data.
- North American countries like the United States and Canada have established regulatory frameworks to protect sensitive data. For instance, in the United States, organizations are subject to various industry-specific regulations, including HIPAA (Health Insurance Portability and Accountability Act) for healthcare and the Gramm-Leach-Bliley Act (GLBA) for financial institutions. Compliance with these regulations helps organizations implement security measures to mitigate data exfiltration risks.
- Organizations in North America implement a range of security measures to protect against data exfiltration. These include implementing robust firewalls, intrusion detection and prevention systems, endpoint protection, encryption technologies, access controls, employee training, awareness programs, incident response plans, and continuous monitoring for early detection of exfiltration attempts.
Data Exfiltration Industry Overview
The Data Exfiltration Market is highly fragmented, with major players like Norton LifeLock, McAfee LLC, Palo Alto Networks, Google LLC, and Fortinet. Players in the market are adopting strategies such as partnerships and acquisitions to enhance their product offerings and gain sustainable competitive advantage.
In October 2022, Fortinet offered networking and security convergence to remote users. FortiSASE now includes a next-generation dual-mode CASB, providing extensive visibility and control for SaaS applications. FortiSASE provides comprehensive visibility into sanctioned and unsanctioned apps by employing inline and API-based capabilities to handle shadow IT and data exfiltration challenges.
In September 2022, McAfee Corp., one of the global pioneers in online protection, announced the launch of McAfee+ in Australia, a new product line including all-new privacy and identity safeguards that enabled users to live their lives online safely and securely.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Buyers/Consumers
- 4.3.2 Bargaining Power of Suppliers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Assessment of the COVID-19 Impact on the Industry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Exponential Growth in the Volumes of Enterprise Data and the Need for Data Exfiltration Prevention Solutions
- 5.1.2 Strict Regulatory Requirements for Data Protection
- 5.1.3 Increasing Incidents of Data Loss in the On-Premises Environment
- 5.2 Market Restraints
- 5.2.1 Compatibility Issues Between On-premises Application and the Cloud Environment
6 MARKET SEGMENTATION
- 6.1 By Organization Size
- 6.1.1 Small- and Medium-sized Enterprises (SMEs)
- 6.1.2 Large Enterprise
- 6.2 By Component
- 6.2.1 Solutions (Encryption, Antivirus, Firewall, Intrusion Detection System, Data Loss Prevention and Other Solutions)
- 6.2.2 Services (Penetration Testing Services, Support and Maintenance, Integration Services, Support and Maintenance, and Consulting Services)
- 6.3 By End-user Vertical
- 6.3.1 Banking, Financial Services, and Insurance (BFSI)
- 6.3.2 IT and Telecom
- 6.3.3 Healthcare and Life Sciences
- 6.3.4 Government and Defense
- 6.3.5 Retail and E-commerce
- 6.3.6 Manufacturing
- 6.3.7 Other End-user Verticals
- 6.4 By Geography
- 6.4.1 North America
- 6.4.1.1 United States
- 6.4.1.2 Canada
- 6.4.2 Europe
- 6.4.2.1 Germany
- 6.4.2.2 United Kingdom
- 6.4.2.3 France
- 6.4.2.4 Rest of Europe
- 6.4.3 Asia-Pacific
- 6.4.3.1 India
- 6.4.3.2 China
- 6.4.3.3 Japan
- 6.4.3.4 Rest of Asia-Pacific
- 6.4.4 Latin America
- 6.4.4.1 Brazil
- 6.4.4.2 Argentina
- 6.4.4.3 Rest of Latin America
- 6.4.5 Middle-East and Africa
- 6.4.5.1 United Arab Emirates
- 6.4.5.2 Saudi Arabia
- 6.4.5.3 Rest of Middle-East and Africa
- 6.4.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 NortonLifeLock
- 7.1.2 McAfee LLC
- 7.1.3 Palo Alto Networks
- 7.1.4 Google LLC
- 7.1.5 Fortinet
- 7.1.6 HP Inc
- 7.1.7 Cisco Systems inc.
- 7.1.8 GTB Technologies
- 7.1.9 Check Point Software Technologies
- 7.1.10 Juniper Networks
- 7.1.11 Hackerone Inc
- 7.1.12 Barracuda Networks
- 7.1.13 Sophos Group plc
- 7.1.14 Zscaler
- 7.2 Investment Analysis
8 MARKET OPPORTUNITIES AND FUTURE TRENDS




