Need help finding what you are looking for?
Contact Us
PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1689693

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1689693
Enterprise Key Management (EKM) - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030)
PUBLISHED:
PAGES: 126 Pages
DELIVERY TIME: 2-3 business days
SELECT AN OPTION
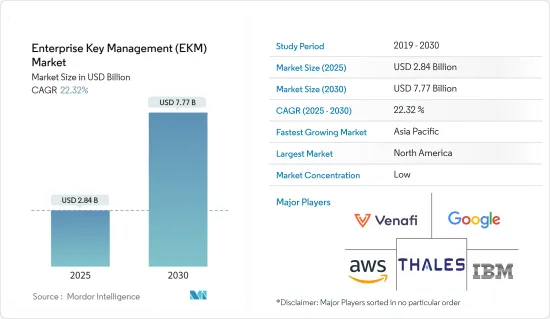
The Enterprise Key Management Market size is estimated at USD 2.84 billion in 2025, and is expected to reach USD 7.77 billion by 2030, at a CAGR of 22.32% during the forecast period (2025-2030).
Key Highlights
- Enterprise key management encompasses the practices and technologies employed by organizations to secure, manage, and control cryptographic keys used for data encryption. As encryption becomes more prevalent in enterprises, the significance of effectively managing these cryptographic key materials amplifies. Enterprise key management systems primarily address the challenges associated with managing cryptographic keys for data at rest. These systems find application across various sectors, including BFSI, healthcare, government and defense, IT and telecom, and retail.
- With the rise in data breaches and the theft of private information, multiple sectors are embracing advanced corporate security solutions. The market's growth is further propelled by organizations transitioning to digital environments to offer digital services and the escalating volume of sensitive data that necessitates protection.
- Enterprises driven by rapid digital transformation seek cost-efficiency and effectiveness through scalability. Technological advancements aid in achieving these goals. However, this digital shift also heightens their vulnerability to data breaches and cyber threats, leading to substantial financial losses.
- The current market grapples with a dearth of skilled professionals, particularly in data analysis. This shortage is especially concerning as data volumes surge, leaving companies struggling to extract valuable insights. This challenge is further compounded in the Middle East, where a smaller cybersecurity workforce makes the region a prime target for data breaches and cybercrimes. Many professionals in this region lack the experience to handle such threats, prompting global companies to invest heavily in cybersecurity training to bolster employee awareness.
Enterprise Key Management (EKM) Market Trends
Cloud Segment to Witness Significant Growth
- Enterprise key management entails the secure administration of cryptographic keys, which are pivotal in data encryption across diverse systems and applications. Opting for cloud-based key management solutions offers advantages like scalability, accessibility, and cost-effectiveness.
- Cloud-based key management systems are highly adaptable, allowing organizations to scale up and down with ease in response to data volume fluctuations. For example, Amazon Web Services (AWS) Key Management Service (KMS) empowers enterprises to create and oversee encryption keys for their data.
- Furthermore, the proliferation of IoT and cloud technologies has led to a surge in data generation. As organizations grapple with the challenge of securing this data, enterprise key management solutions are gaining traction. These solutions enable organizations to encrypt data both at rest and in transit, ensuring only authorized users can access it.
- The exponential growth of IoT devices, which generate copious amounts of data, necessitates robust encryption and key management solutions. These solutions safeguard data as it moves between devices, gateways, and cloud-based applications, driving the market's growth.
- The escalating number of connected devices is fueling a data deluge, often stored in the cloud. According to the Ericsson Mobility Report (November 2023), IoT connections were projected to reach 15.7 billion by 2023 and a staggering 38.9 billion by 2029.
- In today's software industry, where employees use diverse devices and companies operate servers on various operating systems, the risk of cyber threats looms large. This, coupled with the rising adoption of cloud applications, is prompting organizations to invest in cloud security solutions.
Asia Pacific to Register Major Growth
- The growth of enterprise key management solutions in Asia-Pacific is primarily driven by rapid digital transformation, increasing adoption of cloud services, and the rise in cybersecurity threats. As the frequency of cyber threats increases, organizations in the Asia-Pacific region prioritize cybersecurity measures to protect their sensitive data and communications.
- The region is witnessing a substantial increase in encryption usage, mainly in the public sector, retail, technology, and software organizations. The rising trend of the Internet of Things among various end-user verticals, coupled with the trend of an increasing number of IoT and connected devices within the Asia-Pacific region, is a crucial factor facilitating the expansion of encryption, further helping the enterprise key management market to grow.
- By end-user verticals, the IT and telecom sector is likely to grow significantly in the Asia-Pacific region. This is mainly due to rising technological advancements, increasing data quantity, and the implementation of cloud-based solutions. Asia-Pacific's focus on innovation in IT, manufacturing, and industrial sectors creates opportunities for key management solution providers.
- Campaigns like the "Digital India Initiative" are driving the government to adopt robust regulations, legal frameworks, and laws to fight cybercrime. Additionally, the increasing popularity of public cloud computing is causing more enterprises to reallocate their business systems to the cloud. Issues concerning data security, tenant isolation, access control, etc., have gradually become a focal point for these enterprises.
Enterprise Key Management (EKM) Market Overview
The enterprise key management market is semi-consolidated. However, it is dominated by players, including AWS, Amazon Web Services, Inc., Thales Group (Gemalto NV), IBM Corporation, Venafi, and Google Inc. (Alphabet), which are leveraging strategic collaborative initiatives to enhance their offerings, market share, and profitability.
- In November 2023, Intel Corp.-backed multi-cloud security firm Fortanix Inc. launched Key Insight, a new capability in its Data Security Manager platform that allows enterprises to discover, assess, and remediate risk and compliance gaps across hybrid multi-cloud environments. The solution offers consolidated insights and control of all cryptographic keys to protect critical data services.
- In April 2023, WinMagic signed a strategic partnership with Carahsoft Technology Corp., the Government IT Solutions Provider. As per the terms of the agreement, Carahsoft will act as WinMagic's Master Government Aggregator, enabling the Public Sector to access the company's encryption and authentication solutions via contracts with OMNIA Partners and National Cooperative Purchasing Alliance (NCPA), Carahsoft's reseller partners.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
Product Code: 67363
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Force Analysis
- 4.2.1 Threat of New Entrants
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Bargaining Power of Suppliers
- 4.2.4 Threat of Substitutes
- 4.2.5 Intensity of Competitive Rivalry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Optimizing Overall Ownership Cost for Security While Maximizing Operational Efficiency and Security
- 5.1.2 Loss of High Profile Data and Compliance Issues
- 5.1.3 Massive Growth of Data Due to the Adoption of IoT and Cloud Technologies
- 5.2 Market Restraints
- 5.2.1 Lack of Awareness and Skilled Workforce
- 5.3 Assessment of COVID-19 Impact on the Market
6 MARKET SEGMENTATION
- 6.1 By Deployment Type
- 6.1.1 Cloud
- 6.1.2 On-Premises
- 6.2 By Size of Enterprise
- 6.2.1 Small- and Medium-sized Enterprises
- 6.2.2 Large Enterprises
- 6.3 By Application
- 6.3.1 Disk Encryption
- 6.3.2 File and Folder Encryption
- 6.3.3 Database Encryption
- 6.3.4 Communication Encryption
- 6.3.5 Cloud Encryption
- 6.4 By End-user Verticals
- 6.4.1 BFSI
- 6.4.2 Healthcare
- 6.4.3 Government and Defense
- 6.4.4 IT and Telecom
- 6.4.5 Retail
- 6.4.6 Other End-user Verticals
- 6.5 By Geography
- 6.5.1 North America
- 6.5.2 Europe
- 6.5.3 Asia
- 6.5.4 Australia and New Zealand
- 6.5.5 Latin America
- 6.5.6 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 Amazon Web Services Inc.
- 7.1.2 Venafi
- 7.1.3 Thales Group (Gemalto NV)
- 7.1.4 Google Inc. (Alphabet)
- 7.1.5 IBM Corporation
- 7.1.6 Oracle Corporation
- 7.1.7 Hewlett Packard Enterprise Company
- 7.1.8 Quantum Corporation
- 7.1.9 Winmagic Inc.
- 7.1.10 Microsoft Corporation
- 7.1.11 Dell Technologies Inc.
8 INVESTMENT ANALYSIS
9 MARKET OPPORTUNITIES AND FUTURE TRENDS
Have a question?


SELECT AN OPTION
Have a question?


Questions? Please give us a call or visit the contact form.
